RBAC in Data Governance: A Complete Guide for Scalable, Secure Access Across Your Data Estate
What are the main types of access models in data governance?
Permalink to “What are the main types of access models in data governance?”Summarize and analyze this article with 👉 🔮 Google AI Mode or 💬 ChatGPT or 🔍 Perplexity or 🤖 Claude or 🐦 Grok (X) .
Access control models define how organizations grant and manage user access to data. In data governance, choosing the right model is critical for balancing security, compliance, and operational efficiency.
The three most common models are:
- Discretionary Access Control (DAC)
- Mandatory Access Control (MAC)
- Role-Based Access Control (RBAC)
1. Discretionary Access Control (DAC)
Permalink to “1. Discretionary Access Control (DAC)”In DAC, data owners determine who can access their assets. Permissions are assigned at the discretion of individuals, which allows flexibility but increases risk, especially in large organizations.
Best for: Collaborative environments with fewer compliance restrictions.
Example: A data analyst shares a dashboard with a teammate by manually granting them access.
2. Attribute-Based Access Control (ABAC)
Permalink to “2. Attribute-Based Access Control (ABAC)”Access is determined by a set of dynamic attributes,such as user role, department, data sensitivity, location, or time of access.
ABAC offers fine-grained control, making it ideal for complex data environments.
Best for: Large, complex environments with diverse access needs.
Example: A user can access financial data only if they belong to the Finance department and are working within business hours.
3. Role-Based Access Control (RBAC)
Permalink to “3. Role-Based Access Control (RBAC)”RBAC grants access based on a user’s role within the organization. Roles (e.g., Analyst, Engineer, Steward) are centrally managed and aligned with job functions or responsibilities.
Best for: Organizations with clearly defined roles and a need for scalable, manageable access control.
Example: All data analysts have read-only access to sales data, while only the data engineering team can edit it.
DAC vs. ABAC vs. RBAC: A quick comparison
Permalink to “DAC vs. ABAC vs. RBAC: A quick comparison”While each access control model has its unique approach, RBAC remains one of the most widely adopted due to its simplicity and scalability.
Let’s see how RBAC, ABAC, and DAC differ in their approaches to access control.
Access model | Description | Who controls access | Best for |
|---|---|---|---|
DAC (Discretionary Access Control) | Data owners decide who can access their assets | Individual users (data owners) | Collaborative environments with lower security needs |
ABAC (Attribute-Based Access Control) | Access granted based on user, resource, or environment attributes | Policy engine using rules and metadata | Complex environments needing fine-grained control |
RBAC (Role-Based Access Control) | Access based on user roles like Analyst, Admin, or Steward | Central admins defining roles and permissions | Organizations with clearly defined job roles and responsibilities |
How does RBAC work in data governance?
Permalink to “How does RBAC work in data governance?”RBAC in data governance links user roles to specific access permissions, ensuring that only the right people can access the right data at the right time.
Here’s a 5-step process to show how RBAC works in data governance.
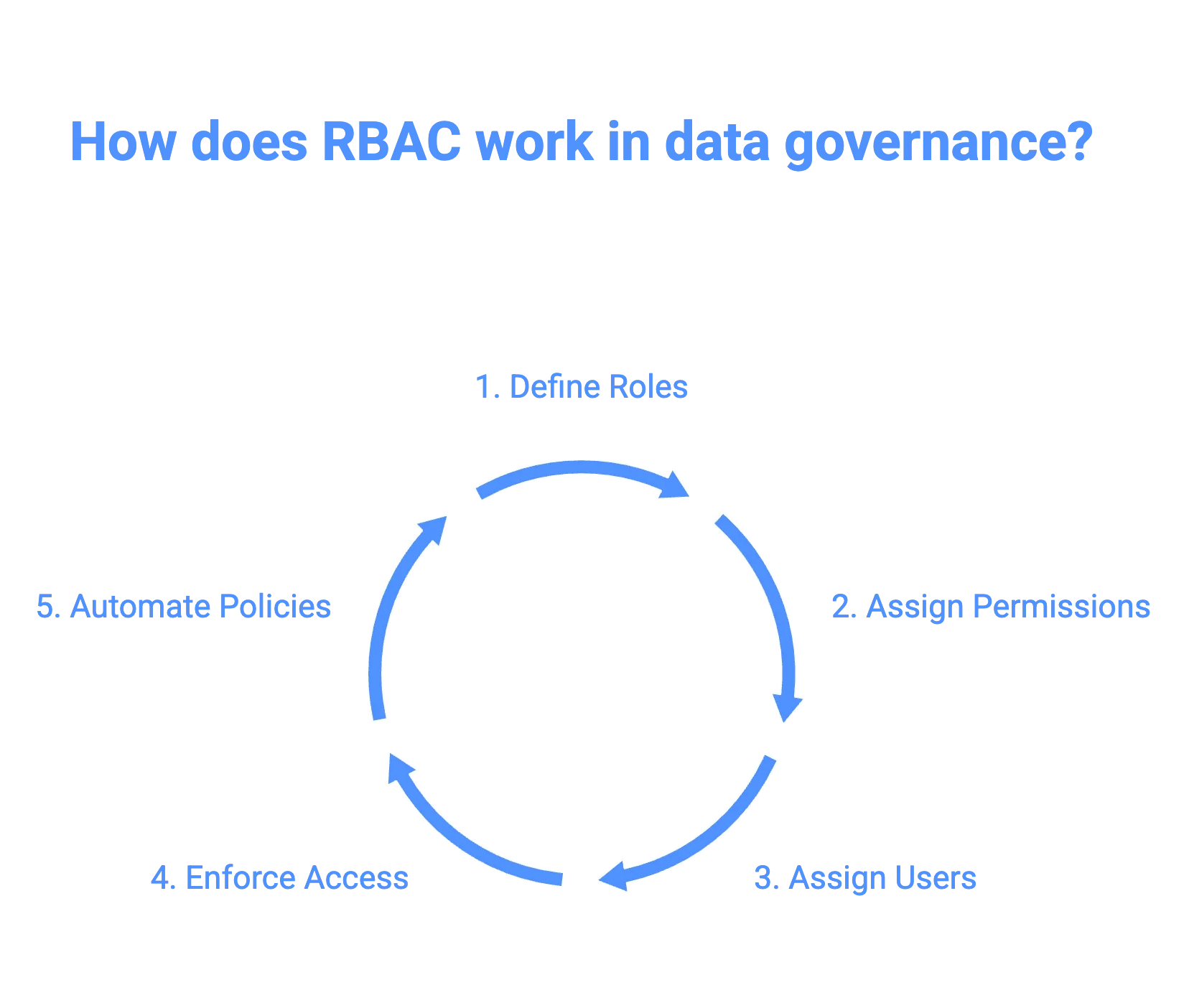
5 steps to implementing RBAC in data governance - Image by Atlan.
1. Role definition
Permalink to “1. Role definition”Roles are created based on job responsibilities, teams, or domains.
For instance, you can set up roles, such as:
- Viewers: Read-only access to data, no modifications.
- Editors: Can modify (update or transform) existing data.
- Admins: Full control, including permissions management and data deletion.
- Stewards: Govern data quality, lineage, and compliance.
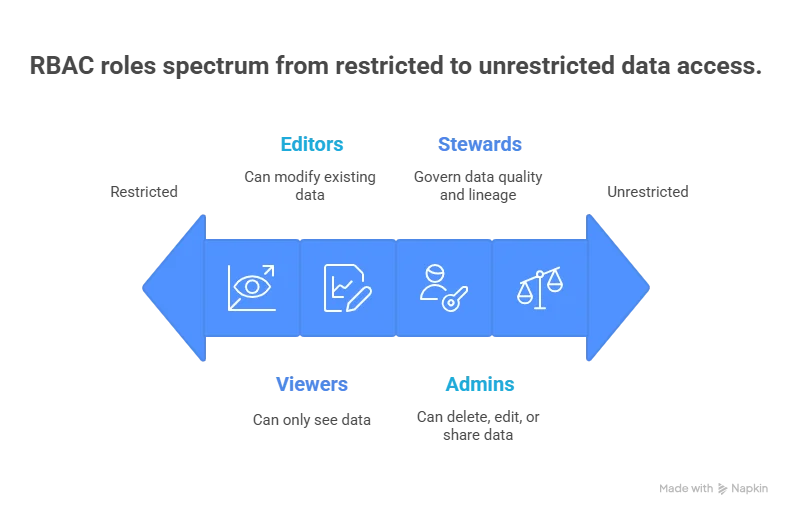
Defining RBAC roles - Image by Atlan.
2. Permission assignment
Permalink to “2. Permission assignment”Each role is granted a specific set of permissions, determining what data they can access and what actions they can perform.
Permissions can apply at various levels, such as:
- Dataset level: Access to specific tables or files.
- Column level: Masking or hiding sensitive fields like SSNs or emails.
- Action level: Permissions to read, write, delete, or share data.
3. User assignment
Permalink to “3. User assignment”Users are assigned to roles that match their job titles, domains, or functions.
Instead of assigning access individually, users inherit permissions from their roles, thereby streamlining administration and scaling securely across teams.
4. Access enforcement
Permalink to “4. Access enforcement”The system enforces role-based rules in real time. Users can only access data that aligns with their assigned role, following the principle of least privilege—granting only what’s strictly necessary.
5. Policy automation
Permalink to “5. Policy automation”RBAC integrates with metadata tagging to automate access control.
For example, a policy can automatically restrict access to assets tagged “PII” for all roles except Admins and Stewards, ensuring consistency, compliance, and lower operational overhead.
What are the benefits of RBAC in data governance?
Permalink to “What are the benefits of RBAC in data governance?”Role‑Based Access Control (RBAC) delivers concrete advantages for data governance, especially in complex, regulated environments. Key benefits include:
- Consistent policy enforcement: RBAC ensures that access rules are applied uniformly across systems, lowering administrative overhead, reducing drift and differences that could introduce vulnerabilities.
- Minimized risk of data exposure: RBAC restricts access to only the data a role requires, following the least privilege principle. This reduces the attack surface and prevents unauthorized access or insider threats.
- Improved compliance and auditability: RBAC provides clear mappings between users, roles, and permissions. Clear role definitions and access logs mean that auditors can quickly determine who accessed what, when, and why.
- Operational scalability: As organizations grow, RBAC scales: new users, teams, or data resources can be accommodated by role assignment rather than reinventing permissions. This ensures minimal disruption to daily operations.
- Faster response during incidents: Because roles are well-defined, in case of breach or misuse, it’s easier to isolate affected roles, modify permissions, and contain damage.
What are some best practices for using RBAC in data governance?
Permalink to “What are some best practices for using RBAC in data governance?”To get the most value from RBAC while minimizing risks, here are 9 best practices to follow:
- Align roles with real responsibilities: Design roles that reflect actual job functions, domains, or data access needs—not just generic titles.
- Apply the principle of least privilege (PoLP): Grant users only the minimum access needed to perform their tasks. Avoid giving blanket or default permissions.
- Enforce tagging and classification policies: Combine RBAC with metadata tagging (e.g., “PII” or “Confidential”) to apply policies dynamically and reduce manual errors.
- Use groups to simplify role management: Consider organizing users into groups like “Marketing Analysts” or “Finance Leads” to apply consistent role assignments at scale.
- Automate role assignment where possible: Automate provisioning and deprovisioning of access based on employee lifecycle events—such as onboarding, transfers, or offboarding. This reduces manual errors and ensures timely access revocation.
- Use standardized access patterns: Implement predictable, RESTful-style permission checks (verb + URL, like
GET /salesorPOST /revenue) to make access enforcement easier and more maintainable. - Separate duties with layered roles: Prevent conflicts of interest by separating roles that involve data access, editing, and governance (e.g., viewer vs. steward).
- Monitor access activity: Track who accessed what and when to support incident response, audit readiness, and continuous improvement in access management.
- Regularly review and audit roles and access: Conduct periodic audits to ensure roles remain relevant, access is appropriate, and inactive users are removed. Involve business units in the review process to ensure that the roles align with current organizational needs.
How can you implement RBAC in data governance with Atlan?
Permalink to “How can you implement RBAC in data governance with Atlan?”Atlan simplifies RBAC by offering an intuitive way to create roles and assign access based on business context.
Atlan’s governance and orchestration platform establishes metadata-driven, policy-enforced access control across the modern data stack. Key capabilities include:
- Define roles aligned to business personas, data domains, or projects
- Govern access using metadata tags (e.g., PII, confidential, business unit, domain, etc.) – so that sensitive data is protected, even inside a dataset
- Automate sensitive discovery and tagging (like PII) across systems
- Propagate policy configurations to source systems like Snowflake using its bidirectional tag sync and metadata context
- Auditable logs and visibility as every role assignment, access event, and change request is tracked. You get visibility into who can see or edit what asset.
Real stories from real customers: Consistent, automated policy enforcement at scale
Permalink to “Real stories from real customers: Consistent, automated policy enforcement at scale”
Modernized data stack and launched new products faster while safeguarding sensitive data
“Austin Capital Bank has embraced Atlan as their Active Metadata Management solution to modernize their data stack and enhance data governance. Ian Bass, Head of Data & Analytics, highlighted, ‘We needed a tool for data governance… an interface built on top of Snowflake to easily see who has access to what.’ With Atlan, they launched new products with unprecedented speed while ensuring sensitive data is protected through advanced masking policies.”

Ian Bass, Head of Data & Analytics
Austin Capital Bank
🎧 Listen to podcast: Austin Capital Bank From Data Chaos to Data Confidence

53 % less engineering workload and 20 % higher data-user satisfaction
“Kiwi.com has transformed its data governance by consolidating thousands of data assets into 58 discoverable data products using Atlan. ‘Atlan reduced our central engineering workload by 53 % and improved data user satisfaction by 20 %,’ Kiwi.com shared. Atlan’s intuitive interface streamlines access to essential information like ownership, contracts, and data quality issues, driving efficient governance across teams.”
Data Team
Kiwi.com
🎧 Listen to podcast: How Kiwi.com Unified Its Stack with Atlan
Let’s help you build a robust data governance framework
Book a Personalized Demo →Ready to operationalize RBAC that scales with your data estate and teams?
Permalink to “Ready to operationalize RBAC that scales with your data estate and teams?”Role-Based Access Control (RBAC) is a foundational component of modern data governance. It offers a structured and repeatable way of managing access by aligning permissions with defined roles.
As data volumes grow and teams scale, RBAC helps ensure that the right people have the right access at the right time. With platforms like Atlan, organizations can make RBAC implementation effective by using automated policy enforcement, column-level lineage, bidirectional tagging, and more.
FAQs about RBAC in data governance
Permalink to “FAQs about RBAC in data governance”1. What is role-based data governance?
Permalink to “1. What is role-based data governance?”Role‑based data governance means defining data access and management rules around roles instead of individuals.
A role like “Analyst,” “Steward,” or “Admin” gets pre‑set permissions. Users assigned to those roles automatically inherit the permissions.
2. What are the three types of RBAC?
Permalink to “2. What are the three types of RBAC?”There are three common sub‑types or styles when implementing Role‑Based Access Control:
- Simple RBAC: Roles are flat and static; permissions assigned directly to roles, little to no hierarchy.
- Hierarchical RBAC: Roles are arranged in a hierarchy where senior roles inherit permissions from junior roles. For example, a “Manager” role inherits all permissions of “Analyst.”
- Constrained RBAC: Adds separation of duties or constraints (for instance, one user cannot hold two conflicting roles) and supports rules to enforce those constraints.
3. What is an example of RBAC?
Permalink to “3. What is an example of RBAC?”Imagine a private equity firm using RBAC for its data governance:
- A Viewer role only has read access to dashboards
- An Editor role can modify investment data tables
- A Steward role oversees data lineage and quality checks
- An Admin role can assign other users to roles and manage permissions.
When a new junior analyst joins, the firm assigns them the Editor role, giving them appropriate access without manually granting permissions per dataset.
4. What are the three levels of access controls?
Permalink to “4. What are the three levels of access controls?”There are three widely recognized levels of access control, each defining how access decisions are made and enforced within an organization:
- Discretionary Access Control (DAC): Access is at the discretion of the data owner.
- Attribute-Based Access Control (ABAC): Access decisions use attributes (of user, resource, environment) via policy rules.
- Role-Based Access Control (RBAC): Access is granted based on the user’s role within the organization.
5. What is the difference between RBAC and ABAC?
Permalink to “5. What is the difference between RBAC and ABAC?”RBAC (Role‑Based Access Control) grants permissions based on a user’s role. It’s simpler to manage once roles are clearly defined, and it works well when organizational roles are stable and well understood.
ABAC (Attribute‑Based Access Control) uses more granular rules. Access depends not just on role, but on attributes like user department, time of request, location, data classification, and environmental conditions.
In practice, ABAC offers greater flexibility and finer control but can be more complex to set up and maintain. RBAC is easier to scale initially. Many organizations use a hybrid approach, combining RBAC for core roles and ABAC for exceptions or edge cases.
6. What are the three primary rules for RBAC?
Permalink to “6. What are the three primary rules for RBAC?”RBAC is governed by three fundamental rules that determine how permissions are assigned and enforced within a system:
- Role assignment: A subject must be assigned a role to access resources.
- Role authorization: Only authorized roles can be assigned to a subject.
- Permission authorization: Subjects can perform only those actions authorized for their role.
Share this article
Atlan is the next-generation platform for data and AI governance. It is a control plane that stitches together a business's disparate data infrastructure, cataloging and enriching data with business context and security.
RBAC in data governance: Related reads
Permalink to “RBAC in data governance: Related reads”- AI for Compliance Monitoring in Finance: Use Cases & Setup
- Unified Control Plane for Data: The Future of Data Cataloging
- Data Governance for AI: Challenges & Best Practices
- AI Governance: How to Mitigate Risks & Maximize Benefits
- The Future of AI Governance: Gartner’s Roadmap for Responsible AI Adoption
- 6 Essential AI Governance Principles for Responsible and Ethical AI Use
- What Is Data Lineage & Why Is It Important?
- Automated Data Lineage: Making Lineage Work For Everyone
- How AI-Ready Data Lineage Activates Trust & Context in 2025
- Data Catalog: Does Your Business Really Need One?
- What Is data governance & why does it matter?
- What is a data governance framework and why do you need one?
- What is data stewardship: Meaning, benefits, and its importance in data governance
- Data Governance Tools Comparison: How to Select the Best
- Data Governance Process: Why Your Business Can’t Succeed Without It
- Data Governance Maturity Model: A Roadmap to Optimizing Your Data Initiatives and Driving Business Value
- Federated Data Governance: Principles, Benefits, Setup
- Data Governance Committee 101: When Do You Need One?
- Data Governance Roles & Responsibilities: A Quick Round-Up
- Data Governance Councils in 2025: Everything You Need to Know
- Data Governance Policy: Examples, Templates & How to Write One
- 7 Best Practices for Data Governance to Follow in 2025
- 7 Must-Have Data Governance Certifications for 2025
- How to Drive Business Value with Data Governance




















