Atlan's Responsible Disclosure Program

Share this article
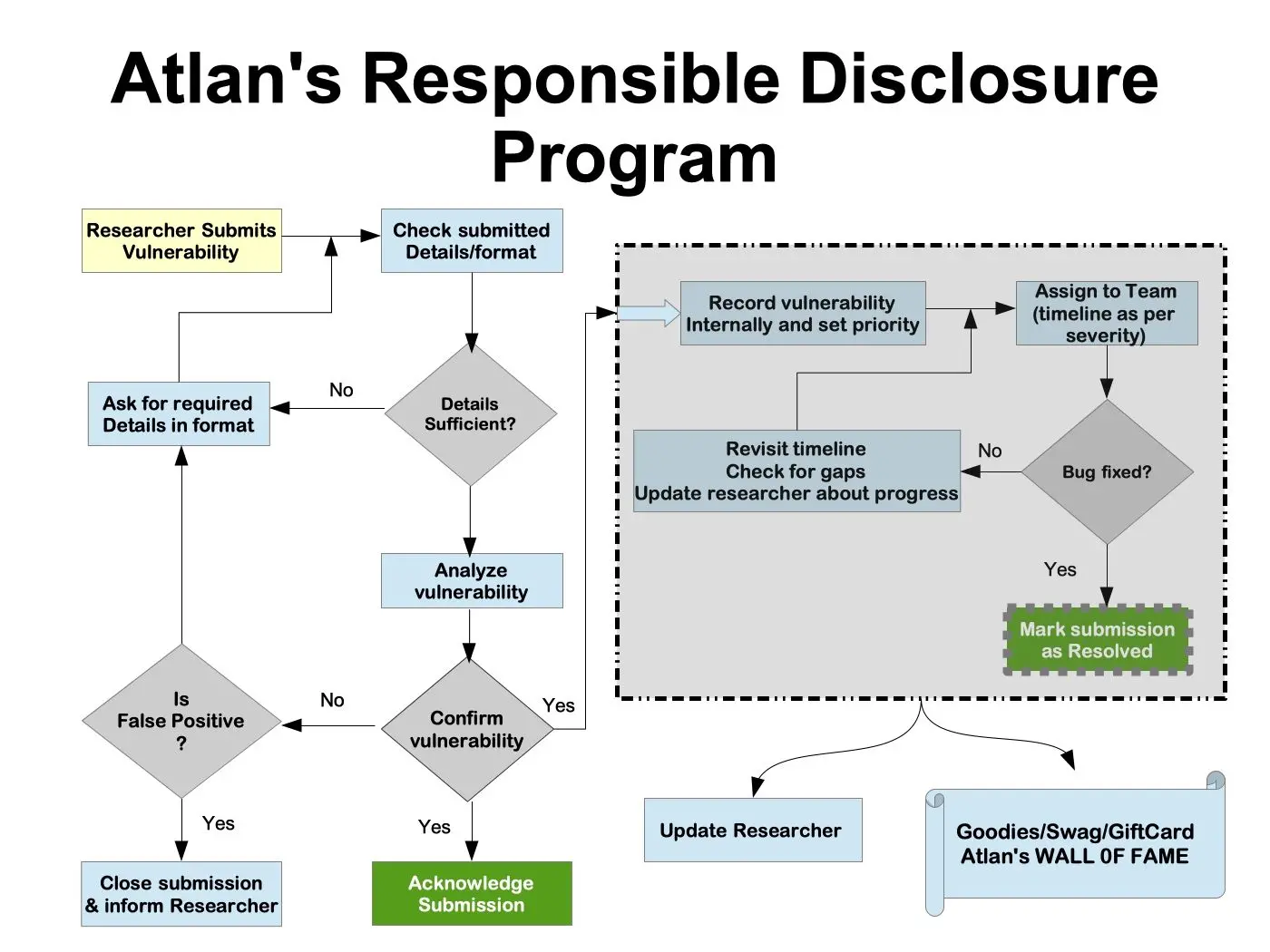
Atlan is committed to maintaining the security of our products, services, and systems. We believe that a responsible disclosure program will help us in achieving this goal.
Atlan's Responsible Disclosure Program allows security researchers to systematically report vulnerabilities found in Atlan's application/services/infrastructure. This helps us to handle and respond to such vulnerabilities in a very organized way.
Please carefully read the program brief for specific rules. These rules apply to all assignments:
- Testing should be performed only on systems listed under the program brief ‘Targets’ section. Any other systems are Out of Scope.
- Except when otherwise noted in the program brief, you should create accounts for testing purposes.
- Submissions must be made exclusively through Atlan’s Vulnerability Submission form to be considered for a reward.
- Communication regarding submissions must remain within Atlan’s Vulnerability Submission Form and/or official Atlan support channels for the duration of the disclosure process.
- Actions that affect the integrity or availability of program targets are prohibited and strictly enforced. If you notice performance degradation on the target systems, you must immediately suspend all use of automated tools.
- Submissions should have an impact on the target’s security posture. Impact means the reported issue affects the target’s users, systems, or data security in a meaningful way. Submitters may be asked to defend the impact in order to qualify for a reward.
- Submissions may be closed if a researcher is non-responsive to requests for information after 7 days.
- We encourage researchers to include a video or screenshot as Proof-of-Concept in their submissions. These files should not be shared publicly. This includes uploading to any publicly accessible websites (i.e. YouTube, Imgur, etc.). If the file exceeds 100MB, upload the file to a secure online service such as Vimeo, with a password.
- Atlan’s Responsible Disclosure policies apply to all submissions made through Atlan’s Vulnerability Submission platform, including Duplicates, Out of Scope, and Not Applicable submissions. Customers may select Nondisclosure, Coordinated Disclosure, or Custom Disclosure policies to be applied to their program brief.
What is excluded? #
Some submission types are excluded because they are dangerous to assess, or because they have a low-security impact on the overall project. This section contains issues that Atlan does not accept, will be immediately marked as invalid, and are not rewardable.
- Findings from physical testing such as office access (e.g. open doors, tailgating).
- Findings derived primarily from social engineering (e.g. phishing, vishing).
- Findings from applications or systems not listed in the ‘Targets’ section.
- Functional, UI, and UX bugs and spelling mistakes.
- Network-level Denial of Service (DoS/DDoS) vulnerabilities.
Non-qualifying submission types #
Some submission types do not qualify for a reward because they have a low-security impact on the program owner, and thus, do not trigger a code change. This section contains a listing of issues found to be commonly reproducible and reported but is often ineligible. We strongly suggest you do not report these issues unless you can demonstrate a chained attack with a higher impact.
- Descriptive error messages (e.g. Stack Traces, application or server errors).
- HTTP 404 codes/pages or other HTTP non-200 codes/pages.
- Banner disclosure on common/public services.
- Disclosure of known public files or directories, (e.g. robots.txt).
- Clickjacking and issues are only exploitable through clickjacking.
- CSRF on forms that are available to anonymous users (e.g. the contact form).
- Logout Cross-Site Request Forgery (logout CSRF).
- Presence of application or web browser ‘autocomplete’ or ‘save password’ functionality.
- Lack of Secure and HTTPOnly cookie flags.
- Lack of Security Speedbump when leaving the site.
- Weak Captcha / Captcha Bypass
- Username enumeration via Login Page error message
- Username enumeration via Forgot Password error message
- Login or Forgot Password page brute force and account lockout not enforced.
- OPTIONS / TRACE HTTP method enabled
- SSL Attacks such as BEAST, BREACH, Renegotiation attack
- SSL Forward secrecy is not enabled
- SSL Insecure cipher suites
- The Anti-MIME-Sniffing header X-Content-Type-Options
- Missing HTTP security headers, specifically (https://blog.veracode.com/2014/03/guidelines-for-setting-security-headers/)
Domain in Scope: #
We request researchers avoid finding bugs on domains that are not listed below. Only reports on domains listed will be considered for rewards.
https://humansofdata.atlan.com/
Recognition – Wall of Fame Page #
Atlan is committed to recognizing the efforts of the researchers.
Once the security vulnerability is verified and fixed as a result of the report, we would like to put your name on our Wall of Fame page.
Of course, we will need to know if you want the recognition, in which case you will be required to give us your name and Twitter handle or LinkedIn Profile — as you wish it to be displayed on our Wall of Fame page.
Will you get a reward/swag/goodie? #
We try our best to recognize the efforts of security researchers. However, you are eligible for rewards only if your reports qualify for the criteria mentioned below.
- Only 1 reward will be awarded per vulnerability. However, vulnerabilities arising from the same issue may be combined together while considering a reward.
- In case the same vulnerability is reported by multiple persons, only the person offering the first clear report will receive a reward.
- Rewards are based on severity, impact, and report quality. Our security team must be able to reproduce the issue from your report.
- Reports that are vague or merely depictions of security best practices are unlikely to be considered for rewards. Reports should include proper reproduction steps, explanations with screen recordings, working code, etc.
- Rewards are paid out in the form of Amazon Gift Cards/Swags/goodies.
Atlan security team commitment: #
Upon submission of a potential vulnerability report, the security team and associated development organizations will use reasonable efforts to:
- Respond in a timely manner, acknowledging receipt of your submission.
- Provide an estimated time frame for addressing the reported potential vulnerability.
- Atlan commits to addressing vulnerabilities determined to be critical within 7 Days from the date the vulnerability is validated.
- Notify you upon fixing the vulnerability.
Where to report vulnerabilities? #
We use google forms to accept reports from security researchers. Forms submitted from any other medium won’t be accepted. Please use this link here.
Share this article











