Third-Party Risk Management (TPRM) Explained: A Complete 2025 Guide

Last Updated on: July 08th, 2025 | 13 min read
Unlock Your Data's Potential With Atlan

Quick answer: What is third-party risk management?
Permalink to “Quick answer: What is third-party risk management?”Third-party risk management (TPRM) is the process of identifying, assessing, and mitigating risks associated with external vendors, service providers, or partners that access or impact your organization’s systems, data, or operations.
TPRM helps ensure that third parties meet your security, compliance, operational, and reputational standards.
Up next, we’ll explore the core components of TPRM, why it matters, common risk categories, and how metadata can support more automated and scalable oversight.
Table of Contents
Permalink to “Table of Contents”- Third-party risk management explained
- Why does third-party risk management (TPRM) matter?
- What are the various stages of the third-party risk management lifecycle?
- How can you optimize third-party risk management? 10 TPRM best practices to follow
- How can a metadata control plane help in strengthening third-party risk management?
- Third-party risk management: Final thoughts
- Third-party risk management: Frequently asked questions (FAQs)
Third-party risk management explained
Permalink to “Third-party risk management explained”Summarize and analyze this article with 👉 🔮 Google AI Mode or 💬 ChatGPT or 🔍 Perplexity or 🤖 Claude or 🐦 Grok (X) .
Third-party risk management (TPRM) helps organizations reduce exposure to external risks, such as cybersecurity breaches, compliance violations, or supply chain disruptions. TPRM alleviates such risks by proactively evaluating and monitoring the third parties they rely on to deliver products, services, or infrastructure.
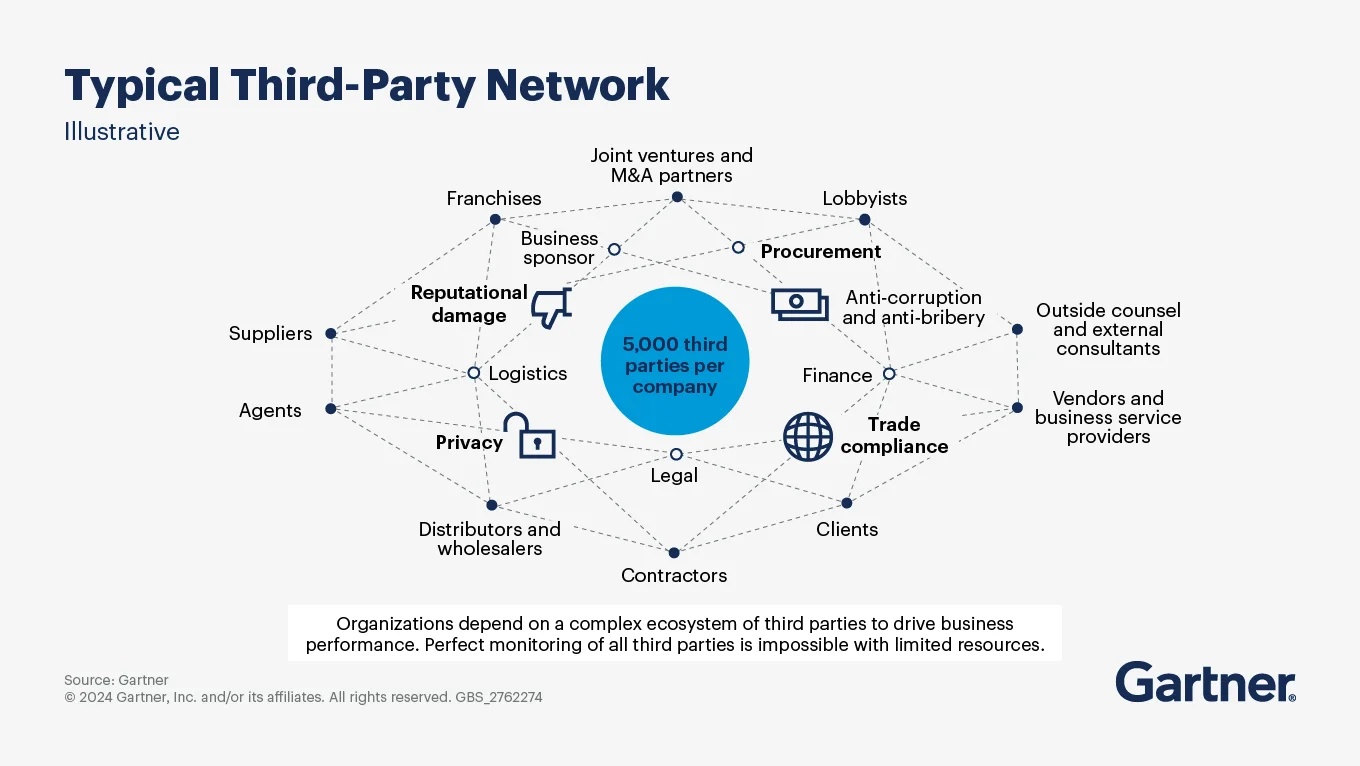
Typical third-party networks - Source: Gartner.
What are some emerging trends and insights on third-party risk management?
Permalink to “What are some emerging trends and insights on third-party risk management?”As third-party networks expand in both size and complexity, organizations are facing heightened risk exposure. According to Gartner:
- There are roughly 5,000 third parties per company and they continue to increase in size and scope.
- 42% of organizations believe third parties are more critical for their businesses now more than ever
- 40% of compliance leaders report that between 11% and 40% of their third parties are considered high-risk.
In response, senior data leaders are taking greater interest in TPRM oversight, and most organizations have shifted governance structures to federated or centralized models.
Meanwhile, many regulators now require organizations to disclose cyber and ESG-related risks.
Why does third-party risk management (TPRM) matter?
Permalink to “Why does third-party risk management (TPRM) matter?”Third-party risk management (TPRM) is essential due to the significant risks associated with external vendors and service providers. These third parties often have access to sensitive data, internal systems, and critical operations, making them potential entry points for cyberattacks, data breaches, or compliance violations.
The risk doesn’t stop there, it extends to fourth parties, such as subcontractors or downstream providers engaged by the third party, further complicating the risk landscape.
In February 2024, Change Healthcare, a core technology vendor for the U.S. healthcare system, was hit by a ransomware attack attributed to the BlackCat/ALPHV group. The breach severely disrupted prescription filling, insurance claims processing, and payments nationwide.
Since Change Healthcare is embedded in mission-critical infrastructure, from billing and payment rails to prescription processing, the attack affected the systems of hundreds of downstream hospitals and providers:
- Hospitals and pharmacies across the country, including major health systems like UnitedHealth Group (which owns Change Healthcare) and Sutter Health, experienced major operational delays.
- Many were unable to process claims or receive payments for weeks, affecting patient care and cash flow.
The attack didn’t just impact Change Healthcare, it rippled across the entire healthcare ecosystem, exposing a lack of visibility and contingency planning for high-risk third parties.
What are the benefits of effective third-party risk management?
Permalink to “What are the benefits of effective third-party risk management?”Proactively managing third-party relationships helps safeguard an organization’s data, reputation, and operational resilience. When effectively implemented, third-party risk management enables organizations to:
- Strengthen operational resilience
- Enhance trust among customers, regulators, and internal stakeholders
- Streamline compliance with evolving regulatory requirements
What are the various stages of the third-party risk management lifecycle?
Permalink to “What are the various stages of the third-party risk management lifecycle?”An effective third-party risk management (TPRM) program follows a continuous lifecycle, helping organizations assess, manage, and monitor risks across the duration of vendor relationships.
The five stages of an effective third-party risk management (TPRM) are:
- Risk assessment
- Risk management setup
- Mitigation planning
- Continuous monitoring
- Audit readiness and documentation
Let’s look into the specifics of each stage.
1. Risk assessment
Permalink to “1. Risk assessment”TPRM begins with an inherent risk assessment to determine the level of due diligence needed. This involves (but isn’t limited to) evaluating the following:
- The third party’s access to sensitive data
- System integration requirements and interoperability
- Geographic exposure
- Regulatory obligations involved (e.g., HIPAA, GDPR, FFIEC)
Based on this, vendors are assigned a risk tier (low, medium, high), which governs the depth of the review.
Questions to ask:
- What policies, processes, and controls does the third party follow to meet your standards?
- Can they comply with laws and regulations applicable to your business?
- How does their information security program align with your confidentiality, integrity, and availability (CIA) requirements?
- How resilient are they to operational disruptions or incidents?
- Have they historically performed well under economic or financial stress?
- Does the third party use technologies that could introduce additional risk? For instance, do they rely on subcontractors, and could that introduce new risks?
2. Risk management setup
Permalink to “2. Risk management setup”For moderate or high-risk vendors, the organization should implement layered safeguards based on risk tiering. Typical safeguards include:
- Contractual protections covering liability, breach notification, confidentiality, and data rights
- Access controls based on least-privilege and secure identity frameworks
- Technical due diligence including encryption, secure APIs, and integration testing
- Business continuity planning with documented RTO/RPO and fallback measures
Questions to ask:
- To what extent does the contract specify each party’s responsibilities—including costs, liabilities, reimbursements, and service expectations?
- What governance and escalation protocols are in place for performance or security issues?
- Does the contract give your organization timely access to information required for monitoring, compliance, or regulatory response?
- What arrangements exist for the use, sharing, and protection of data, technology, and intellectual property?
- Does the contract limit the third party’s data use, retention, and disclosure—especially for customer or sensitive data?
- Are access rights clearly defined to ensure your organization can retrieve its data and records?
- What notice period and process are in place for strategic changes (e.g., M&A, leadership changes)?
- What continuity controls and recovery objectives (RTO/RPO) has the third party committed to in the agreement?
3. Mitigation planning
Permalink to “3. Mitigation planning”Identified risks, whether due to vendor weaknesses or gaps in alignment, must be documented and assigned to responsible teams. Plans may include remediation timelines, internal compensating controls, or technical changes on the vendor’s side.
Questions to ask:
- What are the top risks identified, and who is accountable for remediation?
- What compensating controls will be applied internally if external mitigation is delayed?
- Are there deadlines, milestones, or reporting cycles tied to mitigation plans?
- What tools or mechanisms will be used to track mitigation progress?
- How are risks prioritized based on likelihood and business impact?
4. Continuous monitoring
Permalink to “4. Continuous monitoring”Vendor risk is not static. As the relationship evolves, monitoring ensures early detection of issues. This includes checking SLAs, access logs, regulatory changes, and third-party security certifications.
Questions to ask:
- Is the third party performing its obligations under the contract?
- What performance metrics are tracked (e.g., uptime, response time, SLA compliance)?
- Do audit and test results show effective risk management and regulatory compliance?
- Is the confidentiality, availability, and integrity of your organization’s data being maintained?
- Has the vendor complied with applicable laws, regulations, and service level agreements?
- How are vendor certifications (e.g., SOC 2, ISO 27001) continuously validated and reviewed?
- Has the third party’s financial condition changed, such as declining revenue or rising debt?
- Have there been changes in the vendor’s strategy, leadership, or risk exposure—and what is the impact?
- How often are reassessments triggered by material changes (e.g., scope, location, incident)?
- What tools or integrations support continuous monitoring?
5. Audit readiness and documentation
Permalink to “5. Audit readiness and documentation”Ongoing documentation supports internal audits, external regulators, and board-level reviews. The ability to show risk tiering, controls, performance logs, and incident responses is key to demonstrating compliance.
Questions to ask:
- What documentation exists to show risk assessment, approvals, and tiering?
- Are contract versions, risk mitigation steps, and control reviews archived and accessible?
- Can you produce logs of vendor activities, data access, and policy enforcement if requested?
- How is evidence of continuous monitoring maintained (e.g., dashboards, reports)?
- Are roles clearly assigned for maintaining audit readiness documentation?
How can you optimize third-party risk management? 10 TPRM best practices to follow
Permalink to “How can you optimize third-party risk management? 10 TPRM best practices to follow”As third-party ecosystems grow more complex, optimizing third-party risk management requires a shift from isolated controls to coordinated, proactive governance. These best practices can help reduce risk exposure without bloating compliance overhead:
- Tier vendors by risk exposure: Classify vendors based on access to sensitive data, critical system dependencies, and regulatory implications.
- Embed risk management into procurement: Integrate risk assessment early in the vendor selection process. This ensures alignment between business needs and risk appetite before contracts are signed.
- Develop a clear RACI model: Use a RACI (Responsible, Accountable, Consulted, Informed) framework to clarify ownership of TPRM tasks across compliance, legal, IT, procurement, and the business. Define which teams manage risk assessments, contract reviews, escalation, and documentation.
- Establish centralized or federated governance: Choose a governance model that enables information sharing and cross-functional coordination. Centralized (single-function) or federated (multi-function) models improve coverage and consistency, used by 64% of firms today according to Gartner.
- Clarify ownership with embedded governance: Leverage active metadata to define and enforce ownership across teams, data, legal, security, and business. Use domains, personas, and responsibilities within Atlan to ensure every stakeholder knows their role in managing third-party risk.
- Standardize and automate assessments: Create reusable templates for security reviews, breach notification terms, and regulatory compliance clauses. Automate reassessments and alerts triggered by vendor incidents or contract changes.
- Choose a partner, not a vendor: Pick third-parties that will work with you to take ownership of risks, understand and enforce compliance requirements, communicate openly and frequently about changes in scope, service level, etc.
- Centralize third-party visibility: Use a unified metadata control plane to centralize your third-party inventory, track which vendors have access to what data, when, and why. This setup should also allow you to maintain contracts, assessments, mitigation plans, and monitoring logs in a unified system, supporting audit readiness, streamlining due diligence, and reducing duplicated effort.
- Continuously refresh risk signals: Treat risk assessments as living processes. As vendors evolve or expand access, use dynamic metadata tagging and automated workflows to refresh assessments and flag potential compliance risks in real time.
- Use established TPRM frameworks: While modern best practices offer strategic direction, frameworks provide the structured foundation to operationalize them. Use popular frameworks like NIST SP 800-161, ISO/IEC 27036, Shared Assessments SIG, and OCTAVE Allegro.
How can a metadata control plane help in strengthening third-party risk management?
Permalink to “How can a metadata control plane help in strengthening third-party risk management?”Modern third-party ecosystems are complex, dynamic, and deeply embedded in critical operations. Managing risk across hundreds—or thousands—of vendors requires more than spreadsheets and static inventories.
The biggest challenges in using technology for third-party risk management today include:
- Limited end-to-end support: Most tools focus on onboarding or assessments but fall short on continuous monitoring, change detection, and audit readiness.
- Fragmented visibility across risk terrains: Risk often spans across legal, cyber, compliance, operational, and reputational domains—but most tools only address one.
- Restricted access for primary functional owners: Solutions often gatekeep risk data behind narrow interfaces, making it hard for ERM, compliance, or security leaders to access or act on insights.
- Poor alignment with compliance frameworks: Many tools are generic and not built to reflect your regulatory environment, control objectives, or audit demands.
This is where a metadata control plane like Atlan can help, acting as a connective layer that captures, updates, and distributes context-rich metadata across your organization’s tools and teams, making third-party oversight more automated, real-time, and scalable.
Here’s how it helps:
- Continuous visibility and dynamic context: Atlan connects the dots between vendors, data assets, access patterns, and business impact using active metadata. This provides a living, searchable inventory that evolves in real time
- Ownership clarity through metadata domains: Assign clear responsibilities for vendor data, access rights, and monitoring across legal, IT, and compliance using active metadata personas.
- Cross-functional access and coordination: Role-based views let different owners (compliance, IT, legal, security) access the same metadata, tailored to what they need—ensuring shared context and faster escalation across functions.
- Multi-domain risk mapping: By tagging datasets, systems, and vendor interactions with metadata, Atlan enables you to map third-party exposure across privacy (e.g., GDPR), security (e.g., SOC 2), availability (e.g., SLA terms), and operational domains.
- Policy enforcement and audit readiness: Enforce policies like data minimization or breach notification windows at the metadata level. Maintain tamper-proof records of activity for internal or external audits.
- Trigger-based reassessments: When something changes—like a schema update, elevated access, or contract renewal—Atlan’s workflows can flag the right owners or automatically trigger a reassessment checklist.
- Audit-ready documentation: Every interaction with vendor-related data is logged and traceable. You can generate evidence of access, policy enforcement, and monitoring activities without hunting across disconnected systems.
In short, Atlan helps you replace the fragmented, checkbox-style TPRM setups with a connected, proactive control plane. As a result, risk ownership is shared, compliance is embedded, and third-party visibility is never out of date.
Third-party risk management: Final thoughts
Permalink to “Third-party risk management: Final thoughts”As vendor ecosystems grow in complexity and criticality, so does the exposure to data breaches, operational failures, and regulatory violations. Effective third-party risk management (TPRM) helps organizations stay ahead of these risks by embedding due diligence, contractual safeguards, and continuous monitoring across every stage of the vendor lifecycle.
To truly scale TPRM, organizations need dynamic visibility, cross-functional accountability, and audit-ready traceability. That’s where tools like a metadata control plane help.
Platforms like Atlan enable teams to go beyond risk mitigation, by bringing clarity, control, and coordination to every stage of the third-party data lifecycle. With deep visibility, active metadata, and cross-functional workflows, TPRM becomes an integrated part of how organizations govern and grow.
Third-party risk management: Frequently asked questions (FAQs)
Permalink to “Third-party risk management: Frequently asked questions (FAQs)”1. What is third-party risk management (TPRM)?
Permalink to “1. What is third-party risk management (TPRM)?”Third-party risk management is the process of identifying, assessing, mitigating, and monitoring risks posed by external vendors, partners, or service providers that interact with your organization’s systems, data, or operations.
2. Why is TPRM important?
Permalink to “2. Why is TPRM important?”Vendors often have access to sensitive data or critical systems. A single breach, compliance failure, or operational disruption at a third party can impact your business. TPRM helps prevent these risks and ensures continuity and trust.
3. What are the key stages of the TPRM lifecycle?
Permalink to “3. What are the key stages of the TPRM lifecycle?”The core stages include risk assessment, risk management setup, mitigation planning, continuous monitoring, and audit readiness and documentation.
4. What are common third-party risk categories?
Permalink to “4. What are common third-party risk categories?”Typical risk categories include cybersecurity, regulatory compliance, operational disruption, financial viability, reputational impact, and ESG exposure.
5. What types of third parties should be included in TPRM?
Permalink to “5. What types of third parties should be included in TPRM?”Any external party that handles your data, infrastructure, or business operations—vendors, cloud providers, consultants, SaaS tools, etc.
6. Is TPRM only a cybersecurity concern?
Permalink to “6. Is TPRM only a cybersecurity concern?”No. TPRM covers data privacy, regulatory compliance, operational continuity, and reputational risk, not just cybersecurity.
7. What frameworks can guide a TPRM program?
Permalink to “7. What frameworks can guide a TPRM program?”Popular frameworks include NIST SP 800-161, ISO/IEC 27036, Shared Assessments SIG, and OCTAVE Allegro. These provide structured guidance for assessing and managing third-party risks.
8. How does a metadata control plane improve TPRM?
Permalink to “8. How does a metadata control plane improve TPRM?”It centralizes vendor-data relationships, automates risk signals, supports cross-functional workflows, and ensures ongoing auditability—making TPRM more dynamic and scalable.
Share this article
Atlan is the next-generation platform for data and AI governance. It is a control plane that stitches together a business's disparate data infrastructure, cataloging and enriching data with business context and security.
Third-party risk management: Related reads
Permalink to “Third-party risk management: Related reads”- What is Data Governance? Its Importance, Principles & How to Get Started?
- Data Governance and Compliance: An Act of Checks & Balances
- Data Governance and GDPR: A Comprehensive Guide to Achieving Regulatory Compliance
- Data Compliance Management in 2025
- Automated Data Governance: How Does It Help You Manage Access, Security & More at Scale?
- Enterprise Data Governance Basics, Strategy, Key Challenges, Benefits & Best Practices
- Data Governance in Banking: Benefits, Challenges, Capabilities
- Financial Data Governance: Strategies, Trends, Best Practices
- The Importance of Data Quality in Financial Services: 5 Reasons
- BCBS 239 Data Governance: What Banks Need to Know in 2025
- Financial Data Compliance Software: What Qualities Matter in 2025
- AI for Compliance Monitoring in Finance: Use Cases & Setup
- Unified Control Plane for Data: The Future of Data Cataloging
- Data Readiness for AI: 4 Fundamental Factors to Consider
- Role of Metadata Management in Enterprise AI: Why It Matters


















